collectID is a major problem that impacts industries around the globe. From luxury goods to pharmaceuticals counterfeit goods can cause serious consequences for both business owners and consumers. To address this problem various technology to combat counterfeiting have been created to ensure the authenticity of products and protect consumers. that they are genuine.
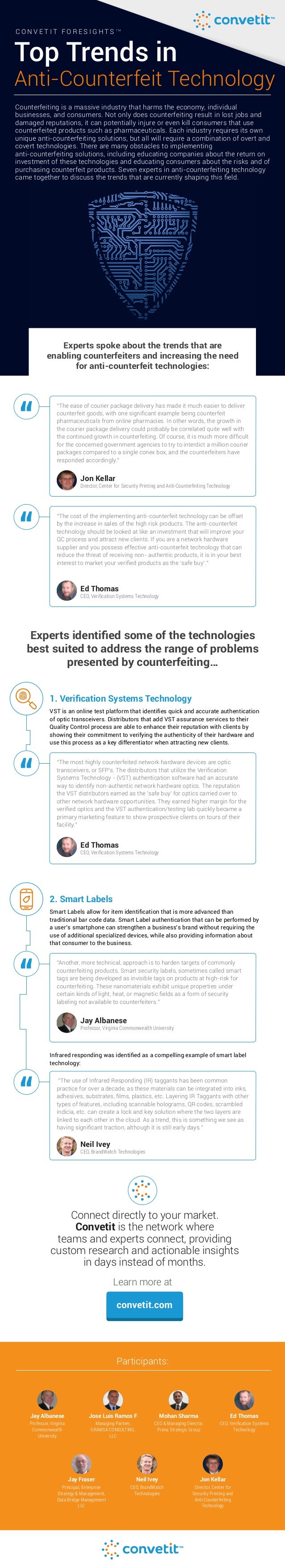
A very commonly used techniques to combat counterfeiting is the use of unique identifiers like serial numbers or QR codes. These identifiers are utilized to identify products in the supply chain, which makes it easier to detect and eliminate counterfeit products. Additionally, these identifiers can be used to verify the authenticity of the products sold to consumers through mobile apps and other platforms that are digital.

Another common anti-counterfeiting method involves the application of holograms as well as other security features on packaging or products themselves. These features can include microtext, watermarks as well as other designs that can be hard to duplicate. They serve as visual cues that help consumers to identify authentic products as well as be utilized in conjunction with other technologies like RFID tags for an integrated security system.
In collectID , the use for blockchain tech has grown into an effective method to monitor and verify the authenticity of goods. By using a decentralized ledger system it provides an irrevocable list of transactions that take place throughout the supply chain. This will allow authorities and businesses to verify the authenticity of products, and make it easier to trace the origin of counterfeit goods.
Another new technology that is getting momentum is the application of RFID tags as well as NFC chips. These tags and chips can be embedded in products, and can be scan by a scanner or mobile device to confirm the authenticity of the product. Additionally, RFID tags and NFC chips can be utilized to monitor the location of goods throughout the supply chain which makes it easier to detect and remove counterfeit goods.
Additionally, technology like biometrics, including fingerprints, facial recognition, and iris scans, are also being used to secure products and guarantee their authenticity. The use of these technologies is to stop unauthorized access to products and can also be used to verify the identity of individuals who handle or transport items.
In conclusion, anti-counterfeiting tools are essential to fight counterfeiting. They provide a way to ensure that they are authentic. From unique identifiers, to holograms, blockchain technology, RFID tags, NFC chips, and biometrics, many technologies are available to protect products, and the use of multiple levels of protection is the most effective way to protect your products. It is essential to be aware that no single technology is 100% secure, and it is important to always keep up-to-date with the latest technology developments to keep ahead of counterfeiters.
